

WHY ARMOR
Because security shouldn’t just defend, it should transform
Growing your business in the digital world shouldn’t mean endless threats or stressful audits. You want clarity, control, and confidence — without the noise and confusion. Armor puts you back in command: real expertise and straightforward tools that make security simple, reliable, and impactful.
0+
Years of experience
0%
Quicker time to compliance
0+
Compliance controls, frameworks including PCI-DSS
0%+
Faster decisions with AI-driven defenses and 24/7 experts
"Compliance is a journey, and we know we can always rely on Armor; they simply make life so much easier. We just went through the highest certification for PCI compliance as a Service Provider, and we could not have done that without Armor’s support."
Stephen Btiggs, CTO, Gala Technologies
"Armor seemed like a great fit and gave us the flexibility we were desiring for the security. They were also incredibly affordable – we were getting security experts as team members, along with getting infrastructure, too."
Jeff Wickham, Director of Product Development, 4MyBenefits
"One of the key things we've found with everyone at Armor is that you can just pick up the phone and say you’ve got a problem. And someone will sit there and listen to you. And then they’ll phone you back 20 minutes later with a solution."
Jonathan Mclachlan, Technical Director, RE:Digital Group
"We are building leading-edge products for the defense, aerospace, and power industries with extremely sensitive data. We believe the performance of Oracle Cloud, safeguarded by Armor, is the sweet spot for our advanced engineering products and technologies."
Karl Schleelein, Senior Infrastructure Engineer, Curtiss-Wright
"At the heart of what we were trying to achieve was more efficient threat detection and response; seeking a single source of truth solution that would provide us with greater global threat intelligence, control, testing and guidance whilst also facilitating large scale growth when required."
Guy Gibson, IT Infrastructure Manager, Colt Data Centres
"Compliance is a journey, and we know we can always rely on Armor; they simply make life so much easier. We just went through the highest certification for PCI compliance as a Service Provider, and we could not have done that without Armor’s support."
Stephen Btiggs, CTO, Gala Technologies
"Armor seemed like a great fit and gave us the flexibility we were desiring for the security. They were also incredibly affordable – we were getting security experts as team members, along with getting infrastructure, too."
Jeff Wickham, Director of Product Development, 4MyBenefits
"One of the key things we've found with everyone at Armor is that you can just pick up the phone and say you’ve got a problem. And someone will sit there and listen to you. And then they’ll phone you back 20 minutes later with a solution."
Jonathan Mclachlan, Technical Director, RE:Digital Group
"We are building leading-edge products for the defense, aerospace, and power industries with extremely sensitive data. We believe the performance of Oracle Cloud, safeguarded by Armor, is the sweet spot for our advanced engineering products and technologies."
Karl Schleelein, Senior Infrastructure Engineer, Curtiss-Wright
"At the heart of what we were trying to achieve was more efficient threat detection and response; seeking a single source of truth solution that would provide us with greater global threat intelligence, control, testing and guidance whilst also facilitating large scale growth when required."
Guy Gibson, IT Infrastructure Manager, Colt Data Centres
"Compliance is a journey, and we know we can always rely on Armor; they simply make life so much easier. We just went through the highest certification for PCI compliance as a Service Provider, and we could not have done that without Armor’s support."
Stephen Btiggs, CTO, Gala Technologies
"Armor seemed like a great fit and gave us the flexibility we were desiring for the security. They were also incredibly affordable – we were getting security experts as team members, along with getting infrastructure, too."
Jeff Wickham, Director of Product Development, 4MyBenefits
"One of the key things we've found with everyone at Armor is that you can just pick up the phone and say you’ve got a problem. And someone will sit there and listen to you. And then they’ll phone you back 20 minutes later with a solution."
Jonathan Mclachlan, Technical Director, RE:Digital Group
"We are building leading-edge products for the defense, aerospace, and power industries with extremely sensitive data. We believe the performance of Oracle Cloud, safeguarded by Armor, is the sweet spot for our advanced engineering products and technologies."
Karl Schleelein, Senior Infrastructure Engineer, Curtiss-Wright
"At the heart of what we were trying to achieve was more efficient threat detection and response; seeking a single source of truth solution that would provide us with greater global threat intelligence, control, testing and guidance whilst also facilitating large scale growth when required."
Guy Gibson, IT Infrastructure Manager, Colt Data Centres
"Compliance is a journey, and we know we can always rely on Armor; they simply make life so much easier. We just went through the highest certification for PCI compliance as a Service Provider, and we could not have done that without Armor’s support."
Stephen Btiggs, CTO, Gala Technologies
"Armor seemed like a great fit and gave us the flexibility we were desiring for the security. They were also incredibly affordable – we were getting security experts as team members, along with getting infrastructure, too."
Jeff Wickham, Director of Product Development, 4MyBenefits
"One of the key things we've found with everyone at Armor is that you can just pick up the phone and say you’ve got a problem. And someone will sit there and listen to you. And then they’ll phone you back 20 minutes later with a solution."
Jonathan Mclachlan, Technical Director, RE:Digital Group
"We are building leading-edge products for the defense, aerospace, and power industries with extremely sensitive data. We believe the performance of Oracle Cloud, safeguarded by Armor, is the sweet spot for our advanced engineering products and technologies."
Karl Schleelein, Senior Infrastructure Engineer, Curtiss-Wright
"At the heart of what we were trying to achieve was more efficient threat detection and response; seeking a single source of truth solution that would provide us with greater global threat intelligence, control, testing and guidance whilst also facilitating large scale growth when required."
Guy Gibson, IT Infrastructure Manager, Colt Data Centres
"Compliance is a journey, and we know we can always rely on Armor; they simply make life so much easier. We just went through the highest certification for PCI compliance as a Service Provider, and we could not have done that without Armor’s support."
Stephen Btiggs, CTO, Gala Technologies
"Armor seemed like a great fit and gave us the flexibility we were desiring for the security. They were also incredibly affordable – we were getting security experts as team members, along with getting infrastructure, too."
Jeff Wickham, Director of Product Development, 4MyBenefits
"One of the key things we've found with everyone at Armor is that you can just pick up the phone and say you’ve got a problem. And someone will sit there and listen to you. And then they’ll phone you back 20 minutes later with a solution."
Jonathan Mclachlan, Technical Director, RE:Digital Group
"We are building leading-edge products for the defense, aerospace, and power industries with extremely sensitive data. We believe the performance of Oracle Cloud, safeguarded by Armor, is the sweet spot for our advanced engineering products and technologies."
Karl Schleelein, Senior Infrastructure Engineer, Curtiss-Wright
"At the heart of what we were trying to achieve was more efficient threat detection and response; seeking a single source of truth solution that would provide us with greater global threat intelligence, control, testing and guidance whilst also facilitating large scale growth when required."
Guy Gibson, IT Infrastructure Manager, Colt Data Centres
"Compliance is a journey, and we know we can always rely on Armor; they simply make life so much easier. We just went through the highest certification for PCI compliance as a Service Provider, and we could not have done that without Armor’s support."
Stephen Btiggs, CTO, Gala Technologies
"Armor seemed like a great fit and gave us the flexibility we were desiring for the security. They were also incredibly affordable – we were getting security experts as team members, along with getting infrastructure, too."
Jeff Wickham, Director of Product Development, 4MyBenefits
"One of the key things we've found with everyone at Armor is that you can just pick up the phone and say you’ve got a problem. And someone will sit there and listen to you. And then they’ll phone you back 20 minutes later with a solution."
Jonathan Mclachlan, Technical Director, RE:Digital Group
"We are building leading-edge products for the defense, aerospace, and power industries with extremely sensitive data. We believe the performance of Oracle Cloud, safeguarded by Armor, is the sweet spot for our advanced engineering products and technologies."
Karl Schleelein, Senior Infrastructure Engineer, Curtiss-Wright
"At the heart of what we were trying to achieve was more efficient threat detection and response; seeking a single source of truth solution that would provide us with greater global threat intelligence, control, testing and guidance whilst also facilitating large scale growth when required."
Guy Gibson, IT Infrastructure Manager, Colt Data Centres
"Compliance is a journey, and we know we can always rely on Armor; they simply make life so much easier. We just went through the highest certification for PCI compliance as a Service Provider, and we could not have done that without Armor’s support."
Stephen Btiggs, CTO, Gala Technologies
"Armor seemed like a great fit and gave us the flexibility we were desiring for the security. They were also incredibly affordable – we were getting security experts as team members, along with getting infrastructure, too."
Jeff Wickham, Director of Product Development, 4MyBenefits
"One of the key things we've found with everyone at Armor is that you can just pick up the phone and say you’ve got a problem. And someone will sit there and listen to you. And then they’ll phone you back 20 minutes later with a solution."
Jonathan Mclachlan, Technical Director, RE:Digital Group
"We are building leading-edge products for the defense, aerospace, and power industries with extremely sensitive data. We believe the performance of Oracle Cloud, safeguarded by Armor, is the sweet spot for our advanced engineering products and technologies."
Karl Schleelein, Senior Infrastructure Engineer, Curtiss-Wright
"At the heart of what we were trying to achieve was more efficient threat detection and response; seeking a single source of truth solution that would provide us with greater global threat intelligence, control, testing and guidance whilst also facilitating large scale growth when required."
Guy Gibson, IT Infrastructure Manager, Colt Data Centres
"Compliance is a journey, and we know we can always rely on Armor; they simply make life so much easier. We just went through the highest certification for PCI compliance as a Service Provider, and we could not have done that without Armor’s support."
Stephen Btiggs, CTO, Gala Technologies
"Armor seemed like a great fit and gave us the flexibility we were desiring for the security. They were also incredibly affordable – we were getting security experts as team members, along with getting infrastructure, too."
Jeff Wickham, Director of Product Development, 4MyBenefits
"One of the key things we've found with everyone at Armor is that you can just pick up the phone and say you’ve got a problem. And someone will sit there and listen to you. And then they’ll phone you back 20 minutes later with a solution."
Jonathan Mclachlan, Technical Director, RE:Digital Group
"We are building leading-edge products for the defense, aerospace, and power industries with extremely sensitive data. We believe the performance of Oracle Cloud, safeguarded by Armor, is the sweet spot for our advanced engineering products and technologies."
Karl Schleelein, Senior Infrastructure Engineer, Curtiss-Wright
"At the heart of what we were trying to achieve was more efficient threat detection and response; seeking a single source of truth solution that would provide us with greater global threat intelligence, control, testing and guidance whilst also facilitating large scale growth when required."
Guy Gibson, IT Infrastructure Manager, Colt Data Centres
"Compliance is a journey, and we know we can always rely on Armor; they simply make life so much easier. We just went through the highest certification for PCI compliance as a Service Provider, and we could not have done that without Armor’s support."
Stephen Btiggs, CTO, Gala Technologies
"Armor seemed like a great fit and gave us the flexibility we were desiring for the security. They were also incredibly affordable – we were getting security experts as team members, along with getting infrastructure, too."
Jeff Wickham, Director of Product Development, 4MyBenefits
"One of the key things we've found with everyone at Armor is that you can just pick up the phone and say you’ve got a problem. And someone will sit there and listen to you. And then they’ll phone you back 20 minutes later with a solution."
Jonathan Mclachlan, Technical Director, RE:Digital Group
"We are building leading-edge products for the defense, aerospace, and power industries with extremely sensitive data. We believe the performance of Oracle Cloud, safeguarded by Armor, is the sweet spot for our advanced engineering products and technologies."
Karl Schleelein, Senior Infrastructure Engineer, Curtiss-Wright
"At the heart of what we were trying to achieve was more efficient threat detection and response; seeking a single source of truth solution that would provide us with greater global threat intelligence, control, testing and guidance whilst also facilitating large scale growth when required."
Guy Gibson, IT Infrastructure Manager, Colt Data Centres
"Compliance is a journey, and we know we can always rely on Armor; they simply make life so much easier. We just went through the highest certification for PCI compliance as a Service Provider, and we could not have done that without Armor’s support."
Stephen Btiggs, CTO, Gala Technologies
"Armor seemed like a great fit and gave us the flexibility we were desiring for the security. They were also incredibly affordable – we were getting security experts as team members, along with getting infrastructure, too."
Jeff Wickham, Director of Product Development, 4MyBenefits
"One of the key things we've found with everyone at Armor is that you can just pick up the phone and say you’ve got a problem. And someone will sit there and listen to you. And then they’ll phone you back 20 minutes later with a solution."
Jonathan Mclachlan, Technical Director, RE:Digital Group
"We are building leading-edge products for the defense, aerospace, and power industries with extremely sensitive data. We believe the performance of Oracle Cloud, safeguarded by Armor, is the sweet spot for our advanced engineering products and technologies."
Karl Schleelein, Senior Infrastructure Engineer, Curtiss-Wright
"At the heart of what we were trying to achieve was more efficient threat detection and response; seeking a single source of truth solution that would provide us with greater global threat intelligence, control, testing and guidance whilst also facilitating large scale growth when required."
Guy Gibson, IT Infrastructure Manager, Colt Data Centres
"Compliance is a journey, and we know we can always rely on Armor; they simply make life so much easier. We just went through the highest certification for PCI compliance as a Service Provider, and we could not have done that without Armor’s support."
Stephen Btiggs, CTO, Gala Technologies
"Armor seemed like a great fit and gave us the flexibility we were desiring for the security. They were also incredibly affordable – we were getting security experts as team members, along with getting infrastructure, too."
Jeff Wickham, Director of Product Development, 4MyBenefits
"One of the key things we've found with everyone at Armor is that you can just pick up the phone and say you’ve got a problem. And someone will sit there and listen to you. And then they’ll phone you back 20 minutes later with a solution."
Jonathan Mclachlan, Technical Director, RE:Digital Group
"We are building leading-edge products for the defense, aerospace, and power industries with extremely sensitive data. We believe the performance of Oracle Cloud, safeguarded by Armor, is the sweet spot for our advanced engineering products and technologies."
Karl Schleelein, Senior Infrastructure Engineer, Curtiss-Wright
"At the heart of what we were trying to achieve was more efficient threat detection and response; seeking a single source of truth solution that would provide us with greater global threat intelligence, control, testing and guidance whilst also facilitating large scale growth when required."
Guy Gibson, IT Infrastructure Manager, Colt Data Centres
"Compliance is a journey, and we know we can always rely on Armor; they simply make life so much easier. We just went through the highest certification for PCI compliance as a Service Provider, and we could not have done that without Armor’s support."
Stephen Btiggs, CTO, Gala Technologies
"Armor seemed like a great fit and gave us the flexibility we were desiring for the security. They were also incredibly affordable – we were getting security experts as team members, along with getting infrastructure, too."
Jeff Wickham, Director of Product Development, 4MyBenefits
"One of the key things we've found with everyone at Armor is that you can just pick up the phone and say you’ve got a problem. And someone will sit there and listen to you. And then they’ll phone you back 20 minutes later with a solution."
Jonathan Mclachlan, Technical Director, RE:Digital Group
"We are building leading-edge products for the defense, aerospace, and power industries with extremely sensitive data. We believe the performance of Oracle Cloud, safeguarded by Armor, is the sweet spot for our advanced engineering products and technologies."
Karl Schleelein, Senior Infrastructure Engineer, Curtiss-Wright
"At the heart of what we were trying to achieve was more efficient threat detection and response; seeking a single source of truth solution that would provide us with greater global threat intelligence, control, testing and guidance whilst also facilitating large scale growth when required."
Guy Gibson, IT Infrastructure Manager, Colt Data Centres
A Top 20 Global MDR Leader by Frost & Sullivan.
A Top 20 Global MDR Leader by Frost & Sullivan.
Following a rigorous evaluation of over 120 global MDR vendors, Frost & Sullivan distinguished Armor as a leader in the 2025 Frost Radar™ for Managed Detection and Response. This recognition highlights our proven expertise in securing highly regulated industries and our forward-thinking approach to cloud-native security. It validates our core belief: that the right security partner doesn’t just mitigate risk — it accelerates growth.
Following a rigorous evaluation of over 120 global MDR vendors, Frost & Sullivan distinguished Armor as a leader in the 2025 Frost Radar™ for Managed Detection and Response. This recognition highlights our proven expertise in securing highly regulated industries and our forward-thinking approach to cloud-native security. It validates our core belief: that the right security partner doesn’t just mitigate risk — it accelerates growth.

Stronger Together.
Our strategic alliances with the world's leading cloud providers are central to how we deliver seamless security. By integrating directly with Microsoft and Oracle, we enhance their powerful platforms with our specialized managed detection, response, and compliance capabilities. This collaboration ensures your security is as robust and high-performing as the cloud infrastructure it protects.
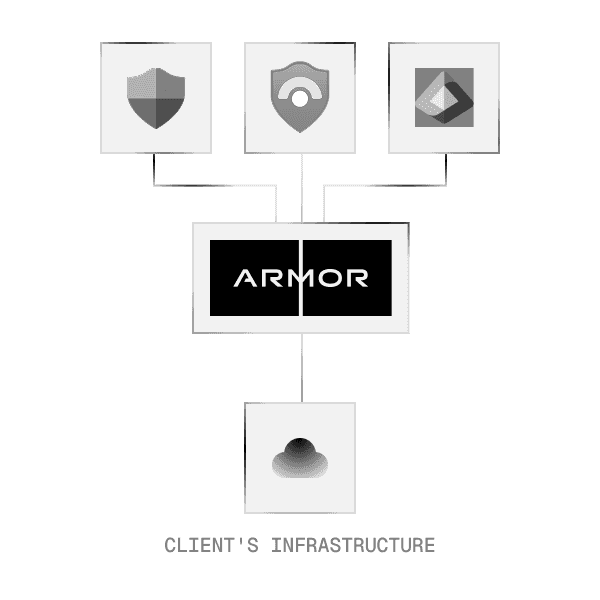

Maximizing Your Microsoft Security.
As a dedicated Microsoft partner, we transform your Microsoft and Azure environment into a resilient, compliant-ready fortress. We don't just work with Microsoft's native security tools - we amplify them.
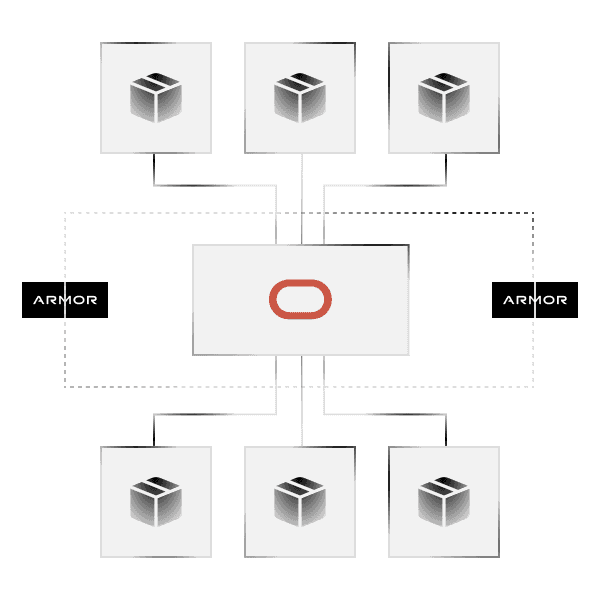

High-Performance Security for Oracle Cloud (OCI).
As an Oracle partner, we extend our battle-tested security to your OCI environment. We protect your most critical workloads with always-on security that strengthens resilience - without sacrificing the performance Oracle is known for.
Where Specialists Bring Clarity
We filter out the noise so you get only what matters, making audits and incident response clear instead of chaotic.
Everything You Need to Stay Secure
Unified protection, without the patchwork.
Our platform puts threat detection, automation, and compliance tools in one place.

Contact
Singapore
City House 36 Robinson Road
Level 04
Singapore 069977
India
8th Floor, AWFIS, Clover Park
Viman Nagar Road
Pune 411014, Maharashtra
United Kingdom
5 New Street Square
London
EC4A 3TW, UK
© 2026 Armor Defense Inc. All Rights Reserved.
Contact
Singapore
City House 36 Robinson Road
Level 04
Singapore 069977
India
8th Floor, AWFIS, Clover Park
Viman Nagar Road
Pune 411014, Maharashtra
United Kingdom
5 New Street Square
London
EC4A 3TW, UK
© 2026 Armor Defense Inc. All Rights Reserved.
Contact
Singapore
City House 36 Robinson Road
Level 04
Singapore 069977
India
8th Floor, AWFIS, Clover Park
Viman Nagar Road
Pune 411014, Maharashtra
United Kingdom
5 New Street Square
London
EC4A 3TW, UK
© 2026 Armor Defense Inc. All Rights Reserved.






