

Our Platform Advantage
Unstoppable Security.
True security isn’t about adding more tools; it’s about creating a single, intelligent system that sees everything and misses nothing. The Armor platform unifies threat detection, AI-powered intelligence, and multi-cloud control into one integrated experience.
Engineered for Clarity and Control
Armor Agent
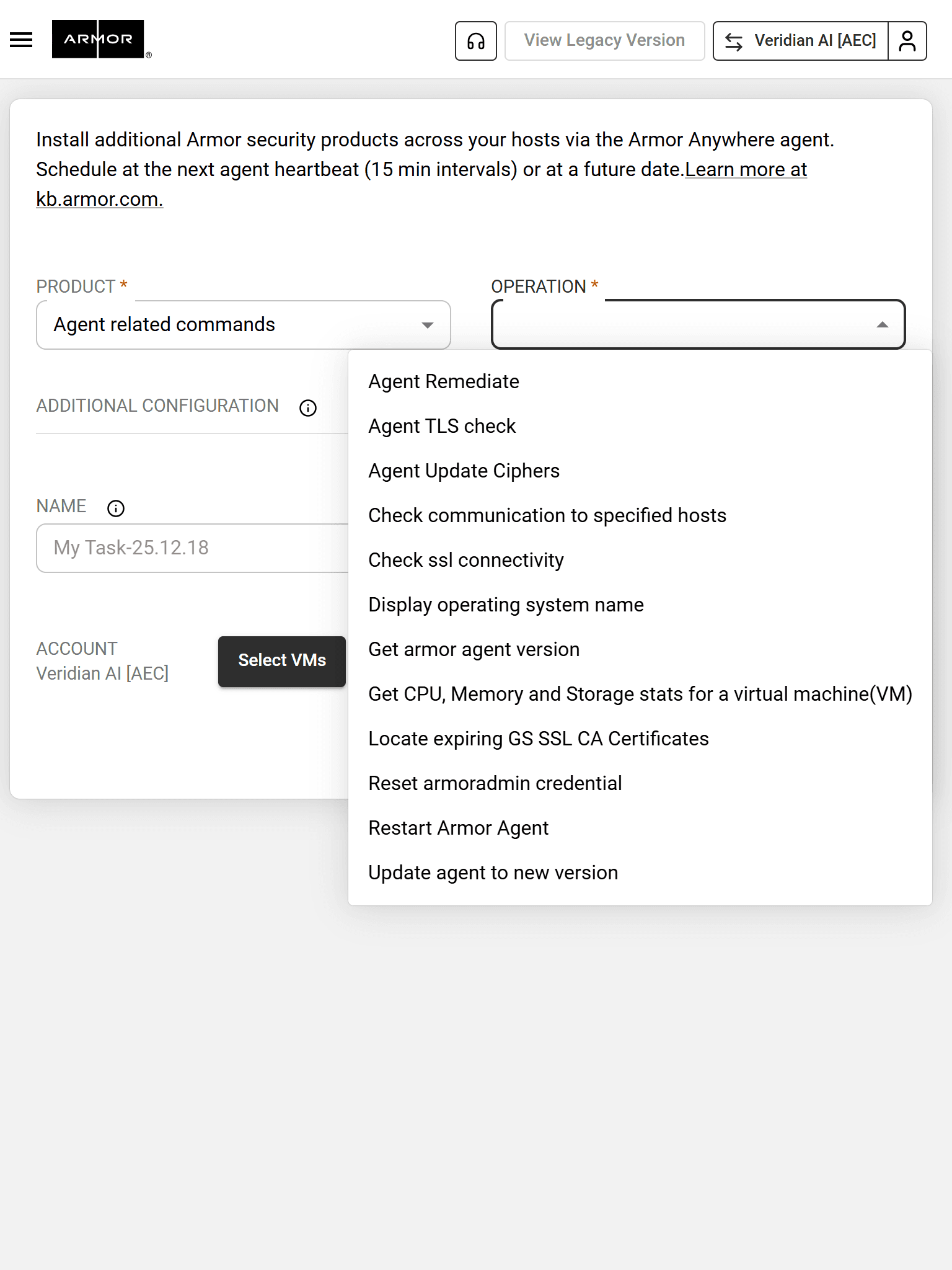
Armor Agent protects workloads with one line of code, combining key security features as your last mile of defense.
Armor Intelligence Platform
The Armor Intelligence Platform uses AI to replicate expert analyst techniques, automating threat data correlation and cutting decision time by up to 95% for faster, more precise threat resolution.
Nexus Portal
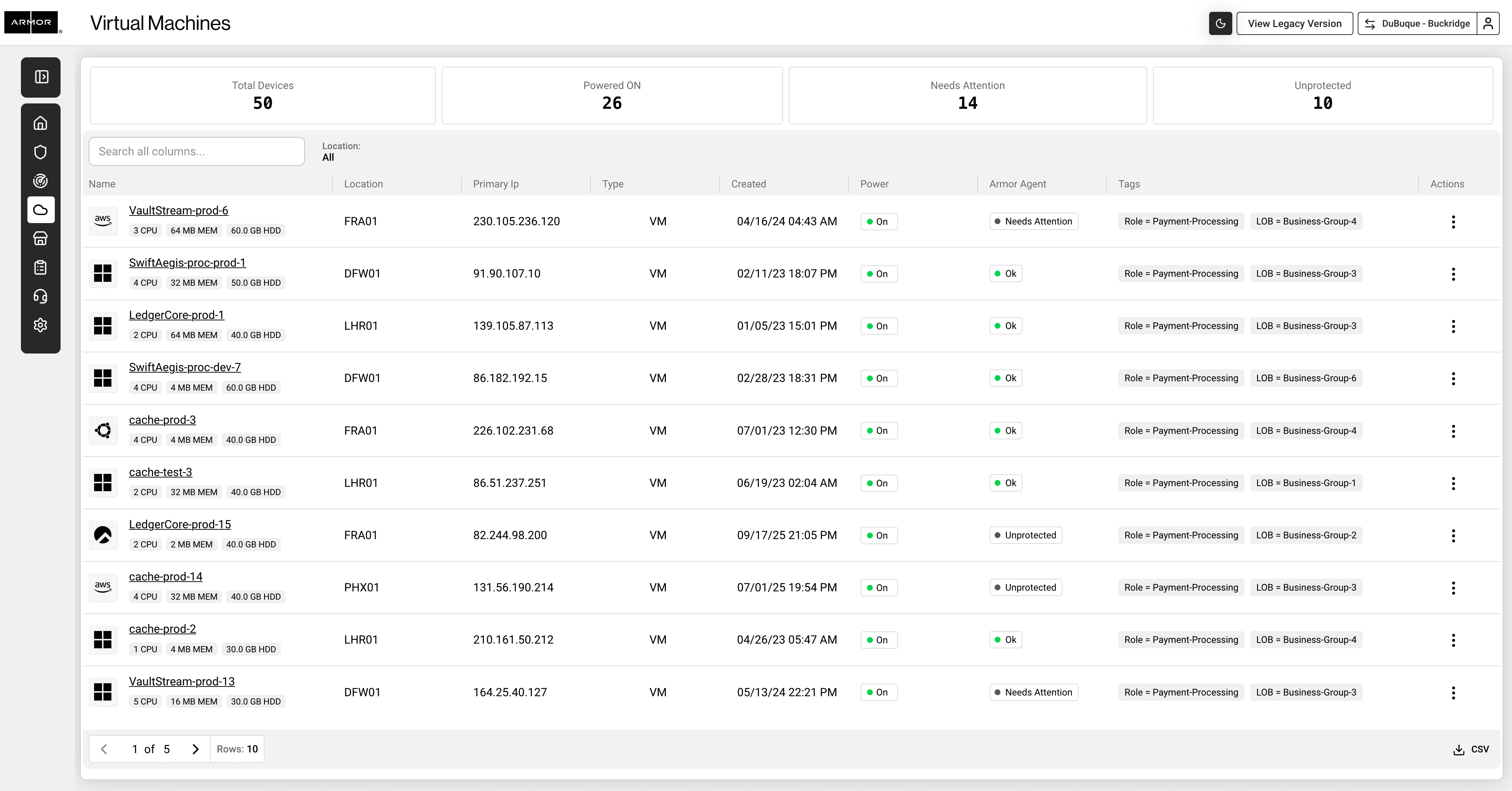
Nexus gives you full visibility into your security operations, showing every detected threat, SOC action, and real-time asset status for transparent, actionable risk management.



Engineered for Clarity and Control
Armor Agent
Armor Agent protects workloads with one line of code, combining key security features as your last mile of defense.
Armor Intelligence Platform
The Armor Intelligence Platform uses AI to replicate expert analyst techniques, automating threat data correlation and cutting decision time by up to 95% for faster, more precise threat resolution.
Nexus Portal
Nexus gives you full visibility into your security operations, showing every detected threat, SOC action, and real-time asset status for transparent, actionable risk management.


Engineered for Clarity and Control
Armor Agent
Armor Agent protects workloads with one line of code, combining key security features as your last mile of defense.
Armor Intelligence Platform
The Armor Intelligence Platform uses AI to replicate expert analyst techniques, automating threat data correlation and cutting decision time by up to 95% for faster, more precise threat resolution.
Nexus Portal
Nexus gives you full visibility into your security operations, showing every detected threat, SOC action, and real-time asset status for transparent, actionable risk management.


Stop managing tools and start managing risk.
See how the Armor platform can transform your security operations and provide the clarity you need to stay ahead of threats.
Contact
Singapore
City House 36 Robinson Road
Level 04
Singapore 069977
India
8th Floor, AWFIS, Clover Park
Viman Nagar Road
Pune 411014, Maharashtra
United Kingdom
5 New Street Square
London
EC4A 3TW, UK
© 2026 Armor Defense Inc. All Rights Reserved.
Contact
Singapore
City House 36 Robinson Road
Level 04
Singapore 069977
India
8th Floor, AWFIS, Clover Park
Viman Nagar Road
Pune 411014, Maharashtra
United Kingdom
5 New Street Square
London
EC4A 3TW, UK
© 2026 Armor Defense Inc. All Rights Reserved.
Contact
Singapore
City House 36 Robinson Road
Level 04
Singapore 069977
India
8th Floor, AWFIS, Clover Park
Viman Nagar Road
Pune 411014, Maharashtra
United Kingdom
5 New Street Square
London
EC4A 3TW, UK
© 2026 Armor Defense Inc. All Rights Reserved.